I have loved Hardware based security for a Fucking eternity, and so I accumulated quite a few different Devices (for the rest of this article, "key" generally refers to the cryptographic keys to avoid confusion) over the years.
so now I am going to compare them.
- The very Simple U2F Stick from Plug-Up
- Yubikey 4 Nano (pre-ROCA)
- Key-ID U2F stick (old model)
- Yubikey 4 Nano (Post ROCA, free)
- Feitian NFC Key (K9)
- Key-ID U2F stick (New model, free)
- Yubikey 5 NFC
- Solo Hacker USB-A
- Solo Tap Secure USB-C
- Solo Secure USB-A
- eWBM (now TrustKey) Goldengate G310 (Free)
- Hypersecu HyperFIDO Mini
- Krypton (not actually a Device)
- Yubico Security Key
- Somu Secure
- Hypersecu HyperFIDO Pro Mini
- Feitian Multipass
- GoTrustID Idem Card
- Ledger Nano S
- Archos Safe-T mini
- Keepkey
- Trezor One
- BitBox02 Multi Edition (purchased, but later also recieved Free Dev Device)
- eWBM (now TrustKey) Goldengate G500
- eWBM (now TrustKey) Goldengate G450
- TrustKey T110
- Onlykey
- Token2 T2F2-AZ FIDO2.1pre (with a free extra)
As you can see I noted that I got 4 of them for free, and because transparency is a given I'll explain the circumstances of each as we go along.
I also do want to stress that aside from the Goldengate, most of this is based on the experience of my life with the thing and not a specific test, but as I got the Goldengate specifically for this purpose I went out of my way to test some things.
Also I will update this post as more stuff comes along, Also do note that I am not ordering chronologically but by theme so I don't have to get overly redundant.
Also as this Article is getting WAY too fucking long already (and I plan adding more devices over time, every device section gets a nice Spoilerbox, so at least scrolling the Version on the site isnt as painful as scrolling in the editor.
Plug-Up U2F
As alluded in the list already this is a VERY simple device. Unlike almost all other Fido-compatible devices this one lacks a button and instead does user presence checks by pulling it out and plugging it in again where I assume, the Stick only waits a few seconds to actually sign something. Currently I can not really get this thing to work, I am not really sure why, but the device is Recognized by the computer, so it is kinda weird.
I would say this device is a nice way to do your very first steps with U2F and was the cheapest at 5€ back in the day (Jan 2016) but seems not to be sold anymore

source: hallaminternet.com 
Source: Wikipedia
Yubikey 4 Nano
Since these two are basically the same I am going to screw the order a bit and do them together. basically the Yubikey is something we in Germany call an "Eierlegende Wollmilchsau", which basically is a (fictional) animal which can provide eggs, wool, milk and meat, basically providing more or less everything one can think of.
Similarly the Yubikey depending on which you got, Provides A LOT of functionality.
The Yubikey 4 to be precise can do the following
- Various modes for Static and dynamic passwords (2 slots), while acting as a keyboard, including a factory provided Yubico OTP, HOTP, and the noted static password
- HMAC based challenge-response (uses the same 2 slots as above)
- Smartcard Features (e.g. Windows Login in Active Directories or using extra tools.)
- PGP Key functionality
- U2F
As you can see, a LOT. U2F works pretty well, which makes sense considering they were among the first to implement it. The other features can be fun to use but especially the password modes are a bit sad considering there are only 2 slots (which is understandable though given that they are accessed by short and long tap of the metal area)
Regarding ROCA, there is essentially a bug in the Yubikey in the RSA generation that the Randomness is garbage allowing the private key to be reconstructed RELATIVELY easily (somewhere in the weeks to months range) and more importantly, in milliseconds one can find out whether a key is affected, allowing someone with interest to easily find out which keys to attack. Afer this came to light Yubico made a Replacement program for all affected Devices, including my first Yubikey 4 Nano. Since U2F is using Elliptic keys though, U2F is entirely not affected and the device is still usable for anything that doesnt involve generating RSA keys on the device.
Yubikey 5
This Device is fairly similar to the 4 Nano as it is also a Yubikey, but basically comes with new stuff.
- NFC (the entire Generation 4 had no NFC)
- Fido2 (PIN based)
- Resident Key storage
The Benefits of NFC are kinda obvious, with supported phones one could easily fo 2 Factor without needing any USB adapters or special USB support which isnt always given.
Fido2 allows the Device to do User Verification, aka, not only confirming that some person is present and pushing it, but also that that person is actually authorized to use that device and therefore key, allowing for a full two-factor auth to occur on the Device and no passwords or otherwise sensitive data to be sent over the internet.
Although with how U2F worked previously with generally the device storing a dynamic half of the key on the website and using a master secret as a second half for the key (simiplified) the big "Problem" is that while it can authenticate a user, a user has to be identified first, for example by entering your username.
Resident keys remove the need for that by the key having a storage space for full keys along with a little bit of metadata (like a display name) which allows the Device to not only verify but also identify the user, basically allowing a Usernameless login which only involves clicking a button on the website to start, tapping your Device, entering your PIN and selecting which key to use (if multiple keys exist for any given website) and you are basically in.
This is very fun, but there are a few problems. Not only is storage space limited, but SECURE storage is generally even MORE limited. The Yubikey 5 can only store (according to what they say) 25 Resident Keys, which isn't really a LOT, and to top it all off, the only way to delete your RKs is to RESET THE ENTIRE DEVICE (in case of the Yubikey specifically only the U2F/FIDO2 module needs a reset), which also wipes the master secret for the normal split keys, forcing you to re-register everywhere when you need to get rid of a usernameless login somewhere.
SERIOUSLY, why am I the one who has to tell companies something so FUCKING OBVIOUS?
SOUNDS LIKE FUN! Imagine a CD-RW where the only way to truly alter data was to reburn the entire disc and you basically only could write new data until it was full if you don't want to reset. Add to this that you cannot backup or otherwise keep a copy of the Keys (granted, this is normal and makes sense), but how can someone miss something so PAINFULLY OBVIOUS!?! (granted they fixed it in a later firmware version, but Yubikeys cannot be updated, so well...
Although if you want a device from Yubico but dont need USB-C or any of the Yubikey-specific feature but only U2F/Fido2, I rather recommend looking at the FAR cheaper "Security Key" lineup from Yubico (below), because while the Yubikey 5 NFC isnt cheap, the smaller and USB-C versions are REALLY getting expensive, and that even more so when getting the 5Ci which has a lightning port to work with iPhones and iPads which recently adopted Support for them.
Yubico Security Key
The Yubico Security Series (I often just refer them as Blue Yubis, as they look very similar to Yubikeys with the most obvious difference being that the Security Keys are blue) are basically much more simple Devices Yubico is offering, unlike the Yubikeys which support borderline every type of authentication in existance as long as you can do it over USB or NFC, the Blue Yubis are focused around the Fido protocols, which currently means U2F and Fido2. There are 3 of them existing, the original, the updated model with support for Fido2 (which can be recognized by a 2 being molded into the plastic) and the NFC version which is basically the 2 but with NFC, while it doesnt have the big 2 in the plastic, the touchbutton has some wireless-style waves around the "key" icon to indicate it being NFC, and as the Blue Yubi NFC only exists as a version with Fido2 it is enough to specify the device.
Basically it has the same functionality as the Fido Module of the Yubikey 5, which generally means:
- Simple U2F support, Tap and go
- Fido2 support with a PIN as UV
- 25 Resident Keys (the lowest I have seen so far)
also depending on the firmware, you get extra features:
- before 5.2.3 you have RSA (nobody really uses that)
- 5.2.3 onwards you have
- RK management
- credential protection (e.g. an RP can say that without UV the device may not even tell the client whether or not a credential is available for use on that speific site.
I specifically got the Blue Yubi NFC for trying out Resident Key management and stuff because it obviously is very awesome to have control over the Resident keys (kinda sad though that I have to declare that as awesome)
The management works generally very well, it needs a PIN to access and generally does what it should, delete keys and so on.
Key-ID U2F Sticks
The old model Key-ID Stick was one of my Favorite U2F sticks and I use it a LOT for dev stuff which apparently led to its downfall, while many Fido Devices have a global counter for better or for worse, this one seems to use separate counters for the different registrations, and while I can use it in some places I still have it registered, it just blocks new registrations entirely, I really liked that this one is small but not too small and has a physical button instead of a touch element, which in case of my Yubi nano seemed quite a bit too sensitive, spawning OTPs left and right...
Due to the fact it no longer registering I got a new model for free to try, which sure is nice but not without its own problems.
It is very small making it easier to lose, or depending where you plug it it, harder to pull out of you don't have a strap attached, also the green light is EXTREMELY bright which while in normal light situations can be annoying, but is really bad when it's dark.
This model does use a global counter though so I don't think it'll easily die like the first.
Hypersecu HyperFIDO Mini
This is the cheapest Hardware device currently available in the entire Lineup.
While it only does U2F, most Sites dont work yet with Fido2 or even Webauthn for that matter, so that wouldn't be an issue. What MIGHT be an issue though is the global, one-step counter (in other words, it always counts up by one, and the same counter is used on all sites) for Privacy reasons. While you generally cannot easily cross-site track a specific device just by its attestation certificate as these are generally assigned not to individual devices, but rather batches of hundreds or even many THOUSANDS of shipped ones of a single model (unless we are talking about custom ones, which are obviously unique). but when observing the counter behavior of Keys with one-step global counters this may lead to a relation over time, although this is generally not very easy.
The Stick is VERY similarly built to the new model Key-ID one (which is why this section is right below this), but has not taken one of the more obvious shortcomings the Key-ID has:

Left is the unbearingly bright new model Key-ID, right is the much less bad HyperFIDO mini. 
symbolic image, Source: Hypersecu
Hypersecu HyperFIDO Pro Mini
the Hyperfido Pro Mini is basically the same as the one without the Pro from the outside but it supports Fido2.
Sadly there is almost no difference between the 2 except for the engraved things like serial number or whatever, but this thing is nothing to sneeze at, because it is with big margin the cheapest Fido2 Stick I got so far for just 11,60€, and even has the second largest RK storage of them all (I counted 128 registrations (seriously, entering the PIN THAT often just is a big pain, so I have been doing it so no one else has to.)
It also has the much less bright light that the normal Mini had in comparison to the Key-ID, which makes it not too bad in my opinion. it certainly does its job nice and seems to be a very good starting point for Fido beginners.
Feitian K9 NFC
Back in the day when I wanted to try U2F on phone you only could use Bluetooth or NFC with the latter being FAR cheaper also needing less care as there isnt any battery needed, and at the time it was the cheaptest NFC key by far (15€ on amazon) It's pretty simple to use with USB you just plug it in and touch when it's blinking to confirm U2F, with NFC, you just slap it on your phone. there isn't really much to say except that I also like the device for being not overly large, but also not too small and just plain working and not having overly bonkers features enabled by default (I read that there is HOTP functionality, but HOTP is borderline never used so cant really try that a lot, and why should I HOTP when I can U2F instead? lol)
Feitian Multipass (K13)
So while originally not cheap, the price has dropped significantly over the years (about 37€), I still won't call this cheap, but it does offer its advantages. the biggest of all is that it combines all 3 relevant interfaces for a portable Fido device (USB, NFC and Bluetooth, making it truly versatile, no matter what device you are interfacing with.
But there's obviously a catch (go figure), it only runs on U2F, meaning for the Future of Passwordless Auth, it sadly is not prepared, but it still makes a very neat second Factor device, I am Happy to have.
But it's slightly awkward form factor makes it hard to find a decent case for it, so accidential activations need to be accounted for (something you should keep in mind when using Bluetooth devices in General)
Solo
The Solo Devices are fairly special for 3 main reasons:
- They are completely open Source (both Soft- and Hardware)
- "Hacker" Editions, which have a completely open Bootloader for doing whatever you want exist for each model.
- They support Updates, meaning you are not forced to buy another Solo if a crazily obvious feature was omitted when you bought your Device, or having to get replacements in case of a vulnerability.
The Solo exists in 4 Base models, which basically falls in the following categories:
USB-A or USB-C
With or without NFC
and of each of those 4 models you can get a Secure or a Hacker variant. basically the secure variant is locked to signed firmware by Solokeys (aka the maker), while the Hacker can be customized however you want, at the cost of not having the real attestation, for obvious reasons.
While I do like the possibility of having hacks I am honestly not really good in programming outside of Web-Stuff (whether that can be considered programming is debatable, I know)
The Solo is very simple to use and while it has a push button that is definitely not weak, the clicky sound is REALLY satisfying, although you really should support the it from below when clicking it to not break your USB port (A version) or plug (C-Version), where you can already see one of the disadvantages of the USB-C Version. while the USB-A version not only has its plug not only as part of the PCB, but also as a result of that, the PCB is REALLY thick, making the USB-A Versions borderline unbreakable, unless you are actively trying to do that (please dont). As the USB-C port does not have the ability to just be a part of the PCB it has to be soldered on, with some newer iterations adding more solder points for stability, but since my U2F lineup generally has it quite rough in my bag, I am not going to take any risks and put my Solo in a case, so there's essentially no way it'll break off that easily.
The Solo supports both U2F and Fido2, same as the Yubikey 5 it uses PIN for verification if asked for it, but as a big step upwards, the solo can store up to 50 Resident keys (not tested), and while they currently dont have any RK management, it is planned, and current customers are not screwed because of the update capability.
Solokeys is also in the process of making a tiny version of the Solo, called the Somu, which basically can be compared with the Yubikey Nano in regards of form factor, otherwise it will be mostly identical to the Solo A, although sadly more expensive, which is understandable though due to being harder to make obviously.
one of the few things that arent perfect on the Solo though is that while it does offer the super awesome feature of colored silicone cases, there isnt any truly transparent place for the light to shine through, so the LED's color gets filtered by the case color making some colors harder to see depending on the case, like when the Solo goes yellow for an authentication, on a blue case it's just green because the Red part gets filtered more strongly than the green, opposite on a red case, where it looks a lot more Red than anything else.

Green Light 
Yellow Light 
Blue Light
In case you live in the US (otherwise shipping will be expensive) you can buy them using this (afiliate) link (no discount, don't blame me for the URL):
https://solokeys.com/discount/my1
Somu
The Somu basically is a MUCH smaller version of the Solo, basically what a Yubikey nano is to a Yubikey, the Somu is to the Solo.
So it has the same basic features as a Solo USB-A with also a Secure and a Hacker version existing.
Frankly there is not much to say about this what hasn't been said about the normal Solo already.
It mostly exists to permanently stay in a USB port like for example a Laptop or PC. That way you dont have to fiddle around with the big Sticks and can just lightly tap the side of your Laptop or whatever and use that to do your Fido needs.
Also, in case you live in the US (otherwise shipping will be expensive) you can buy them using this (afiliate) link (no discount, don't blame me for the URL):
https://solokeys.com/discount/my1
eWBM/TrustKey Goldengate G-Series
for starters first things first: as lined out on the top I got my G310 for free (I literally just asked for it lol) for review purposes, and I am honestly sad that as it stands currently, that I will have to send it back in January (although understandable, as it isnt really a cheap device) and now I can keep it, which makes me happy.
The Goldengate Series is as advertised by eWBM, the first Fido2 Device with an L2 certification, which certainly is a nice thing. It also is the first Fido2 Device I own that uses Fingerprints instead of PIN.
The Goldengate Series consists of 4 different Models where 2 are essentially completely equal (G310/G320) except for one having a USB-A and the other having a USB-C port. the other 2 (G450 and G500), according to eWBM, only differ in shape.
the fingerprint reader works mostly well, at least if you actually take care of scanning your complete finger. it doesnt ask for that many scans, and you sadly don't get an option to continue scanning that finger to get a better image, so be a bit careful with enrolling, also after you stored your fingerprint you have no way to rename them or knowing which is which, so be careful to keep track or just delete them if you want to reorganize.
Also, when putting the G310 onto a USB extension cord (I know it's not part of the USB spec but guess what, I don't care) and then try to use the FP reader in basically any rotation imaginable, it works all the time, if you are careful and put your finger nicely onto the reader, so that's very nice.
One thing you might wanna know though is that while the Stick allows for 15 false FPs before locking itself, after every 3 tries it will require a reboot, basically pulling it out and plugging it in again, which is the same other Fido2 keys require for the PIN, and the PIN runs on 8 tries, same as other Fido2 devices, as per spec.
biggest annoyance is that you need the Bio Manager to unlock the FP scanner though.
If you have Windows 10 1903 or later, the Goldengate is essentially seamless to use as W10 1903+ has "Security Key" Management options in the account Settings part of the PC settings. on other OSes you can (or rather have to) use the Goldengate Bio Manager to enroll your Fingerprints, which did work nice on my WIndows 8.1, although the sofware sometimes gets weird errors and basically needs a quick restart of itself or a replug of the stick. One thing I REALLY like though is the fact that you can at least Quickstart without using any software or Fingerprint Setup. in case there are no FIngerprints set, the FP management PIN doubles as Fido2 Auth PIN and vise versa, basically if you want to sign up to a site which forces Verification with a fresh Goldengate, you will be asked to create a PIN which you can use for Login while you have no Prints, and then later use the same PIN to manage your FPs, which is a really nice feature.
One fun thing to note aside though is that they TOTALLY lied in my face (well not actually as it happened in twitter DMs).
They said the stick can store up to 200 Resident Keys (which already is 8 times Yubi or 4 Times solo, but after I went though with my Resident key registration loop script I got 242 before the device started complaining, which definitely is a nice number. although this thing REALLY gets slow with RKs if you have over 100 keys on that specific site you try to use (although let's be real, that's borderline never going to happen unless you purposely try this). but what I didn't like is that yet again, they also have no way to delete RKs without wiping the entire Stick -.-
Sure while this probably wont happen too often with a keyspace that big, when it DOES happen it is so much more devastating.
Well whatever, also while I was told that they plan to add this into their Bio Manager, I frankly am not sure whether their firmware even supports doing something like that, and OF COURSE there are no updates as they consider an update process that is doable by users as insecure (lol signatures are a thing)
BIG Update: eWBM LIED TO ME
(Quick Note: obviously being sarcastic here)
So I based my statement on the fact that the Goldengates don't run RK Management on statements I got from eWBM in the VERY Long Twitter PM thread where I basically had a whole mix of stuff between complimenting them for good stuff, offering my ideas on things that were maybe not ideal and straight ranting about things I REALLY hated, as well as due to the fact that it kinda took a while for a device to arrive, poking a metric fuckton of questions about the thing so I am prepared for when it arrives and can already point out stuff without actually having to have the Device yet. This includes the very obvious question on whether the device has RK Management as pinpoint-grilling is something I consider kinda important (obviously) and they said that "Deleting resident key is not allowed at this time" and also later on, I quote:
no serious key vendors will allow updates
eWBM (Twitter PM)
on firmware
As a big fan of the Solo Lineup I honestly kinda take a bit offiense in that, also not to forget that allowing updates basically is a low-effort way of doing something for the environment as you can fix stuff without having to make new devices and stuff, which takes energy, resources etc.
This very obviously makes it very easy to assume that they have no firmware way of removing RKs and without buying new ones never will have.
But:
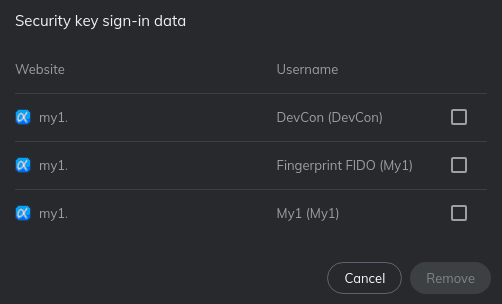
Now this is just pure awesome. This thing not only has WAY more RK storage than most people will need their whole LIFE, but also has credential management AND an optional FP reader in case they want more usability? even as the most expensive USB-A Fido2 device this thing looks awesome from SO MANY points of view that I am not only thinking about trying to get one permanently to use a primary, but also making it very interesting for people who dont use fingerprints.
another Update: too happy too soon
so after trying out a bit more apparently I was too happy too soon, as it turns out, that on my G310 the Resident Key Feature is kinda borked when working with multiple RPs (I should have tested this earlier, lol) where it (maybe, just theorizing) uses a loop to get through the keys and list them, but forgets to actually raise a counter or move a pointer to the next RP in line as it only shows the keys from the last used RP, but as often as there are RPs with RKs on the Device.
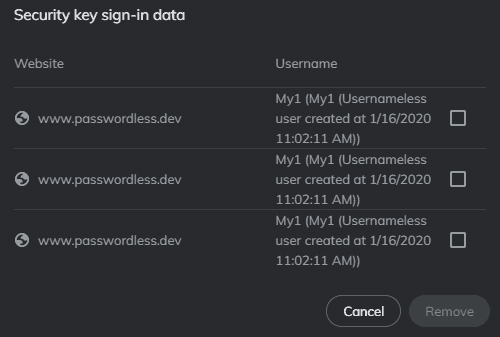
This obviously makes this a LOT of "fun" and while I honestly have no idea how the deletion is supposed to work with that I think I can do some testing in the future as there may be some workarounds to at least not be completely out of luck with these.
While it is very nice to not have to enter a PIN all the time for login, the device has some kinda interesting properties, like that in U2F mode (aka using the CTAP1 protocol), the Goldengate enforces fingerprints if set (orange LED), or I really love that their LED sends mixed signals, even though they have a multicolor LED which can blink and stay bright. for example a cyan blinking can stay for either fingerprintless CTAP2 Auth (either because there are no FPs yet, or the UV is set to discouraged) or A DEVICE RESET, SOUNDS FUN, I know. Blue Flashes can mean either enrollment or CTAP2 with FP, which sure is less devastating but still.
Although one big thing the LED has over all the others is that it not only is a multicolor LED (aside from this and the Solos are have single color (green) LEDs except the Plug-Up which has none at all, is that the Solo's LED colors are kinda obscured by the colorful cases and the fact the LED is basically in the center of the button. The Goldengate basically has a window for the LED next to the FP reader.
in general aside from some chaos with specific interactions of different clients (sometimes Edge on W10 1903+ won't recognize RKs registered on a different client), which are not really fault of the device, this one is the easiest to use, which really makes it nice.
While this is fun and all one thing I need to know is that the BioManager they have for setting the thing up is currently Windows (7 and up) and Mac, so currently there is no way to do Fingerprint setup on Linux (but you can at least use the PIN for basic use).
MOAR Updates: G450/G500
The G450 is more shaped like a traditional USB-Stick and is more likely to fit between USB-Plugs side by side, but the FP Sensor is smaller, also it has a "full" USB-A Plug with Metal rather than the plastic half-plug of the G310, which can be nice for some. The G500 is just HUGE, the design is fairly cool and it in my opinion fits perfectly at things like a USB-Port at the side of a Keyboard, especially with it being a bit angled I could easily any of the 4 left "fingers" (does the thumb count as a finger?) with it sticking out the left of my keyboard with ease, and even without that if you grab it on an extension cord it just FEELS liek triggering something. Also the G500 comes with a case already which is really appreciated considering the distinct shape, and aside from some scratches for obvious reasons it stood pretty well in my bag pocket full of other FIDO Devices.
TrustKey T120 (and T110)
The Trustkey T-Series (They could have chosen a better name like pewdiepie lol just kidding) is basically very similar to the G-Series that they already have, except for a few main differences.
- There is no FP Sensor anymore just a touch area
- No Color LED, just white
- RK Limit is set to 150 (might have not even had a fixed limit in the G310 I blasted with RKs)
- (for the keys I have) RK stuff actually works as intended, this means not only that you dont seem to get duplicated RKs like on the G-Keys I have but also that RK management doesnt time out when full.
All in all i would say this is a cheaper alternative to the G-Series, and the firmware seems a lot more mature now. I would guess on newer G-Series keys the firmware matured too but I dont want to buy a Key I already have just for a damn firmware Update because they cannot be updated so far.
Krypton
Now this one is completely different.
This is a completely software-based U2F thing which runs on Android or iOS for Key storage and uses a plugin for Firefox and Safari, as well as Chromium and its derivatives to do the work on the browser.
It basically does a cryptographic pairing to your computer to make sure only computers that are authorized can use the keys stored and to do a pairing it is required (at least on Android) to pass the Security Method (PIN, Pattern FP etc), if set. Due to the Security of the Cryptographic pairing the devs are confident enough to not only allow using the app with notifications with the style of "do you want to sign in to github.com" or whatever, but also in a completely silent mode for any computers you trust enough, where it just silently answers any requests done immediately and you get in, basically your PC effectively acting as your Second Factor. There is basically only one Secure assumption and that is the pairing process. if you add a bad computer, especially with the Silent mode, it gets very messy very quickly.
While it does use the Keystore or Secure Enclave for Android and iOS respectively, it still is mostly software based and may be vulnerable to attacks full Hardware implementations do not have, so I would be very careful on whether or not to use it or what computers to pair it with.
One good thing privacy-wise is that they use seperate counters and with phones generally having more space I don't think (or at least I hope that) the same issue as with my old Key-ID won't happen with this.
One bigger "problem" although it probably is more a workaround than anything else is that the signatures falsify the User Presence flag. Generally speaking, a Device using Webauthn is supposed to return a flag whether the user was Physically present (in Meatspace) or not during Auth, and it SHALL NOT be set if no UP test has been performed, yet it does. Although granted Webauthn does not account for Silent checks, and website may respond weirdly to a properly-tagged silent auth.
Standards aside there are a couple things that can get really annoying. Not only does it also Silently register (and you cannot control silent register and Silent Sign-in seperately) if it doesnt exist already, which makes not only sandbox testing REALLY annoying, but also makes it so you essentially have to register Krypton before any other Fido Device. Also if you don't use Silent mode the Request notifications never go away, which is really annoying. For Silent mode you can choose whether or not to send a notif although I personally recommend using that so you at least know when you have been signed in and can take measures if it wasnt you.
Idem Card
So while I did get this nifty little thing for free, I did NOT get it from the maker but from a friend across the pond, and I WILL not be positively biased just for something like that.
so let's bring the first thing across. 60$ is REALLY not cheap, but this device IS pretty cool when you first look at its base specs.
I mean you not only have NFC and a chip on this card-like device, but also BLUETOOTH, no fucking joke, this thing has an integrated Battery AND can use it to run Bluetooth, and that's not even all. Alledgedly (I don't have this thing long enough to tell) this thing can run 60 days based on 10 logins per day or 120 days standby, ONE HUNDRED FUCKING TWENTY DAYS, that's 4 MONTHS (well almost, lol), but yeah I am not believing this until I see it, but if it can do that that's pretty damn impressive. also nice, if you do not have an NFC reader or Bluetooth at hand, but a contact based smartcard reader, you should be able to use that to run it too (due to the fact the NFC protocol originated from the one used on contact chips, although, not all work. I had success with a very Simple USB reader and one built into a Laptop, but the ReinerSCT cyberJack RFID komfort just did not want to recognize the card via contact chip (NFC does work tho), don't ask me why, that's just how it is), on the other hand the cyberJack RFID basis (a simple NFC reader originally intended for the German ID card which I got as a free extra in a like 5€ computer magazine in 2010, back when Germany was subsidizing these things left, right and center to get people to use the electronic functions of the new ID card) works just like a BEAUTY.
That is until we get to the major, and I mean MAJOR roadblock of this thing at least for me:
Compatibility
sadly FIDO methods that are not based on the HID method USB generally uses, are NOT supported in Browsers themselves, this leads to the fact that you can only use a device like this on a device where you have support on the OS Level. This results in currently the only supported OSes for this device being
- Windows 10 1903 or later
- Android
- iOS
basically any Desktop that runs on an older windows (like me usually running 8.1 if I need Windows) or a wholly different operating System (like Linux or Mac) basically is out of luck with this card.
THIS SUCKS BIG!
adding insult to injury when trying some stuff around with some special Tools I noticed that the card I got doesn't even properly adhere to the FIDO2 spec (some data has to be ordered a certain way and if the application is strict about it, well bad for you), and they told me that that was done INTENTIONALLY in a way to work around something chrome tried on mac with Bluetooth (and iirc threw away again), and they fixed it in later batches, but how could it be different:
This Card CAN NOT be updated
you cannot imagine how hard I wanted to facepalm when I read that they did that intentionally on a device that cannot be updated. (but I decided I'd rather want to live so here I am)
the fact that this card cannot be updated was known to me prior to all of this as I did ask around long ago, but that they would try something THIS stupid is beyond me. honestly that this goes through as "FIDO2 Certified" is even worse. In my opinion, the Fido Alliance should make it that devices MUST offer updates if
- they deviate from the spec
- use a spec that is marked as preview
as these more often than not can lead to some serious issues, which just sux (see eWBM section above)
Ledger Nano S
So now for my newest Toy which I probably wouldn't have bought if it weren't for the recent 50% off coupon sale Ledger ran. We have the Ledger Nano S, some people may wonder why I bring a cryptocoin Wallet in here, while others may have noticed what's going on.
The Ledger is made to be expandable and Expand they DID (and still do). There is a U2F Applet for this device and they are also developing a FIDO2 applet (no ETAs or progress reports tho, so we might still need to wait quite a bit for that.)
but what we DO know is that the ledger will support the txAuthSimple extension of WebAuthn, which is BIG, as there are currently only 2 makers out there that make devices with Screen and FIDO stuff. one is obviously Ledger, the other is Trezor, and while they DO support FIDO2, that is only on the FAR more expensive Model T (180€) and the Trezor One which is similarly prices as a Ledger Nano S, can only do U2F and I doubt that FIDO2 will reach the Trezor One considering that FIDO2 exists already and there is already feature disparity as well, so even when the Model T gets TxAuth in FIDO2, as that's currently not done yet and on low prio, the Ledger will still be MASSIVELY cheaper.
So most people probably won't know what txAuth even means so let me explain.
for example in Online Banking when you have to enter a transaction number (or do some other confirmation step), wouldn't it kinda be nice to know WHAT you are confirming? In Germany there have been sometimes more sometimes less proprietary methods to do so, where you have a device which either stores a key or accepts a card which instead has the key, then you scan some kind of code or just enter the transaction data) and if you scanned a code the device will actually SHOW YOU what the code contains so you can see the transaction you get the TAN for.
and txAuth is similar. basically you can add some text (or an image in case of txAuthGeneric) to your FIDO2 request and the device will actually show that to the user and sign that thing along.
This is very helpful for example could a website throw in some text about the login location or on an action needed to confirm show what is being confirmed and so on. This is the first step of replacing antique and/or proprietary methods with a standard that is open, which is always nice.
Also for obvious reasons this also means that the Ledger Nano S is updateable which is even more awesome, so any issues can be fixed directly without needing to replace devices or throwing out devices that perfectly work just to get a new feature in.
Archos Safe-T Mini
More Cryptowallets? OH YEAH!
The Safe-T Mini is a mixed bag. It is a relatively inexpensive device at 20€ but also has some SERIOUS drawbacks.
For Starters it isnt overly awesome at its original purpose as it only supports relatively few crypto assets, but putting that aside we have other purposes.
So this device runs U2F only, same as the Ledger, BUT sadly the firmware, which is open Source on Github, hasnt seen any changes for almost 2 years by now, which is REALLY sad, HOWEVER Archos apparently allows flashing custom firmware, so throwing in a FIDO2 firmware might be possible, maybe even without all the cryptocoin stuff.
Also Same as a Ledger, This device's keys are generated using a seed Phrase which encodes a 256 bit master key, which can be restored. This can be seen as convenience but also as a problem for the Security, but what makes this feature pretty bad is the issue that the U2F Counter starts at 1 after Recovery, while on Ledger as you have to install applets and stuff it automatically sets the counter to the current Unixtime (which may become an issue 2038), to set the U2F counter to anything you need a python tool which basically is a commandline management tool for this provided by the maker.
Same as with Ledger, you are kinda hopeless without extra Software.
The worst is by far the recommended setup through there website where you have to install some weird bridge that runs in the background as a service and all.
The big difference tho is WHY you need software. On Ledger you need to install the U2F applet as the firmware is modular, while here as This device is basically a fork of the Trezor One, it needs a computer for setting up the Keys and takes some entropy for that from the computer (but also has some own so an evil computer cannot just seed the RNG and get expected results, but all the features are part of the Firmware, so U2F does not need any extra Setup.
also the recovery process is kinda hilarious and at least for the default one, not in a good way. basically you enter the words in scrambled order INTO YOUR COMPUTER and if you use less than 24, you will enter some extra random decoy words words to fill up the 24.
This is not an awesome way for recovery even if this is orchestrated by the device (aka which words you have to enter will be shown ONLY on the device screen), especially with just 12 words (luckily not the default for this device) when you recover twice with the same phrase on infected computers and the attacker is aware, they can just cross out which words werent in both attempts and it's highly likely they get just the real 12 as mutual words, and unscrambling these is a piece of cake as it literally is just 29 bits of entropy, basically nothing. and even on 24 words, you have 79 bits, which is a bit meh at least. when you can consolidate a lot of power, unscrambling that might not be that much of a problem, it might be now, but the future is usually there to be annoying in that regards.
The second type is a matrix-style input where you get a 3*3 (after the 3rd input of a word a 2*3) grid which shows letters and/or ranges of beginnings of the words and the layout of the matrix is randomized. it's a bit annoying to enter but a lot more useful for safer recovery as the computer is not aware of the matrix layout or anything
well let's get to the actual main part of the Review, the FIDO Stuff.
as I said no FIDO2, just U2F and you need to set the counter yourself on recovery.
but the obvious advantage is as with Ledger, the Display, even without FIDO2, as you can at least see WHO you are signing for, well partially.
As U2F gets the "appid" only as hash, it cannot display the website name directly. however for a few selected sites, the hashes are stored so they can be shown, and for most of these even with an image, which is really helpful at least for these.
for all other sites you get a middle-truncated hash, which shows the first and last 4 bytes (8 hex digits), which isnt too bad either and is imo a bit better than paging through all the hash or just blindly confirming because it's too much of a hassle.
What is also a bit sad is that the error handling is not ideal. When you try to login but this device wont help you it says that right on the screen, however when you want to register but you already have this device it asks whether to authenticate, which is confusing.
The Real issue
This device has however one critical flaw which I cannot miss. It has 4 so called "Secure Zones" and if you set up a PIN and forget it (or someone resets the device without providing the correct PIN (including maxing out the retry counter) this thing will basically blow up one of these zones, making it unusable, and if all 4 are gone, this device will de facto be E-Waste, which is NOT fun.
Trezor One
The Trezor one as the Safe-T Mini and the Ledger Nano S and the Keepkey is also primarily a Cryptocoin Hardware Wallet with U2F being more a side-feature.
Considering the Safe-T Mini is basically a 99% clone of the T1, U2F behaves very similarly between the two. in a few cases the display can show a human readable name, yet in most it will not and instead just show the beginning and end of the appID-hash.
However unlike the Safe-T mini and Ledger, the Trezor only uses normal microprocessors rather than for example a secure element which means the keys inside can be read out with tools and methods that would definitely nothing for the laymen but compared to the other's definitely a lot more doable.
The Main advantage however of the T1 compared to its obvious clone is that the trezor generally speaking still gets firmware updates and if they can make the unification between the T1 and the Trezor Model T firmware (the latter supports FIDO2) that would be a big improvement. Also I am gonna note that I am not intending to test the Trezor T due to its high price tag of 180€ which while for a crypto wallet, can be worth it, would be plain bonkers for a FIDO device.
Keepkey
The Keepkey is yet another Hardware wallet having U2F more as a side thing however their way of using the display is nothing short of beautiful.
Not only is the screen plain HUGE making it easy to read (in the dark at least as it's fairly glossy)
In Fact, when you register and sign into a website using U2F on it, rather then the Safe-T or the Trezor or Ledger, despite being forked from Trezor Firmware does something fairly interesting.
If the Website isnt in the small list of accepted websites, it will take the first 44 bits of the appID-hash, which in case of my1.dev where I have my sandbox would becbfc883093dca10d8d97f079aafa4712fa71af97c0f47a8ce2a2754fa68f6598
and the four words are slogan tone around chicken. This, while being a bit less secure than a hash for comparison, is a LOT easier to remember or at least recognize. and is just awesome in general. the keepkey, while being a lot more dissimilar from its origin, uses the same PIN mechanism as the Trezor One and Safe-T mini, yet the restore mechanism is WILDLY different. while T1 and Safe-T either let you enter the words in random order, significantly reducing the entropy, or using a grid pattern to enter words via ranges of letters, the keepkey uses a polyalphabetic substitution scheme where on each character, the table changes, making it effectively impossible to get any letters out and there dont even need to be any complicated rotors or other enigma-style stuff, as there is no need for a key to be kept in advance as the user sees the substitution table all the time and if decent, the Keepkey will just pull out the new tables at random.
BitBox02 Multi
Yup, the storm of the HW Wallets hasnt ended yet. This time the Bitbox02 Multi Edition. First off, despite being called Multi, it's very minimalistic in its support for Cryptocoins, only having Bitcoin, Ethereum and Litecoin as base coins available, but this is not a review for cryptocoin stuff, so let's get to the FIDO Stuff.
The Bitbox originally displayed the first half of the AppID-Hash, which was pretty normal, yet as I got a dev device when I asked about testing firmwares and stuff and I just for fun actually drilled around in the FW improving upon the Screensaver idea they had, obviously not the Original Idea I just HAD to try out when I got the chance, I later also changed the U2F hash display to be the same as the Keepkey (I did not take any code I just took an educated guess when I saw the words first and later just used that to code the things into the bitbox with a mix of agent-Ransacking the hell out of it and Google/Stackoverflow.
2 Things that makes the bitbox different from the other HW Wallets are the unique approach to Open Source while still including a secure element in a trustless manner (generally as they have NDAs attached open source is hard with these) as well as the backup Paradigm on it. not only can you backup at will unlike the others where you can backup only once and in case of Ledger and Keepkey only directly on setup) the bitbox also makes you to backup to an mSD card. while much less transparent method, it is safe from most kinds of eavesdropping and as long as the mSD never sees a computer, phone or similar device that can exfiltrate the data I consider it to be pretty decent, but it also offers the classic 24 words you can use on other hardware wallets, even if for the purpose of FIDO-ing they are mutually incompatible sadly.
Onlykey
Yubikey in Open Source is something I wouldnt really consider an overstratement of the Onlykey.
Not Only does the onlykey offer up to 2 profiles with 12 slots for passwording and general 2FA stuff, but the second profile can be set into plausible deniability mode, also having features for GPG and public-key stuff but for the obvious reason of being listed here it also can do FIDO stuff. It has FIDO2 including support for CTAP2.1 which is in my opinion fairly important especially as the Onlykey only has 12 RK slots (not sure if per profile or in total, but still a fairly small number) also pretty interesting is the fact that the onlykey is primarily unlocked via a PIN entered throu a keypad with the digits 1-6 and a PIN needing to be 7-10 digits in length. it is pretty damn versatile which makes the onlykey an interesting choice for people who need a do-it-all authentication device.
Token2 T2F2-AZ
So when I heard that Token2 has a FIDO2 device with CTAP2.1 (yes, it's pre, but I think at the point that yubico has been selling these without noting that 2.1 is still preview is just splitting hairs) and that for a pretty competetive price (15€) I cant just say no to it, so I got it, but I also got, for free a pre-release FIDO2 device which I was kindly asked not to say anything about as it's all in a VERY early stage and basically nothing is solid yet, and I agree that I shouldnt raise unwarranted expectations.
The T2F2 one supports HOTP/TOTP along the FIDOing and has 50 RKs, including management which is helpful when you need more than just FIDO, also it has a nice clicky button and also a protective-spin cover which is nice although one obviously needs to note that the button is literally on the spinning axis and therefore on the outside, not being protected by the cover so it's not invincible. to being destroyed, although this would make it a very nice base to make a USB-C version of as the USB-C connector usually is more vulnerable to breaking off compared to the USB-A plug which on many devices is either literally part of the PCB or housing of the device itself making it a lot harder to break off than a C-Port which is just soldered on.
There is also a version of this Device without CTAP2.1pre but rather CTAP2.0 for 1€ (so 14€) less which likely is otherwise completely the same, I havent tested it because I think when CTAP2.1 gets finally properly released and not just withheld to Yubico and the other big ones, that over time fewer and fewer models with 2.0 will be released and I highly recommend that I you want to get this from Token2 to get the 2.1 version. There is also an NFC version for 17€ altho that's sadly also just 2.0.
Comparison
To be updated
firstly the objective table showing the basics of all the models I looked at above
| Name | Mode | Button | UV | Interface | Price | Store |
|---|---|---|---|---|---|---|
| Plug-Up | U2F | None | none | USB-A | N/A | |
| Yubi 4 (nano) | U2F | Touch | none | USB-A | 40€ (big) 50€(nano) | mtrix |
| K9 | U2F | Touch | none | USB-A NFC | N/A | |
| Yubi 5 | Fido2 | Touch | PIN | USB-A NFC USB-C Lightning | 46€ (A+NFC) 51€ (A-Nano) 51€ (C) 61€ (C-Nano) 69€ (Ci) | mtrix |
| Blue Yubi | Fido2 U2F | Touch | PIN | USB-A NFC | 18€ (U2F) 20€ (2) 26€ (NFC) | mtrix |
| Key-ID | Fido2 | Push | none | USB-A | 10€ | Amazon |
| HyperFIDO mini | U2F | Push | none | USB-A | 5,50€ | Amazon |
| HyperFIDO Pro Mini | FIDO2 | Push | PIN | USB-A | 11,60€ | Amazon |
| Solo | Fido2 | Push | PIN | USB-A USB-C NFC | 20€ (A) 25€ (C) 35€ (A+NFC) 40€ (C+NFC) | Amazon |
| Somu | Fido2 | Touch | PIN | USB-A | 35€ | Amazon |
| eWBM | Fido2 | Touch | FP PIN (if no FP) | USB-A USB-C | 54€ (G310) 54€ (G320) 66€ (G450) 100€ (G500) | Pointblank |
| Krypton | U2F | notif none | none | Internet | Free | N/A |
| Multipass | U2F | Push | none | Micro-B NFC BT | 37€ | mtrix |
| Idem Card | Fido2 | Touch | PIN | NFC BT Chip | 60$ | Amazon USA |
| Ledger Nano S | U2F | push | PIN (forced) | micro-B | 60€ | Ledger Store |
| Name | Mode | Button | UV | Interface | Price | Store |
secondly, the subjective Table giving a quick look of what I like and dislike about each one, some of these may seen as good by some people (or it doesnt matter to them), but it should be on attention point at the very least.
| Device | good stuff | stuff for attention |
|---|---|---|
| Plug-Up | was VERY cheap | no button, doesnt work very well anymore |
| Yubi 4 (nano) | very small, can do a LOT | nano very sensitive to touch, accidential activate not cheap |
| K9 | NFC for cheap | nothing so far |
| Yubi 5 | nano exists VERY versatile RK Management on later revisions | Few RKs (25) no delete on earlier revisions generally not cheap due to versatility the later models get more expensive |
| Blue Yubi | trades versatility for cost RK Management on later revisions | Few RKs (25) no delete on earlier revisions |
| Key-ID | nice and cheap | (old model) died due to overuse (new model) LED WAY too bright |
| HyperFIDO Mini | cheapest for U2F | one-step global counter |
| HyperFIDO Pro Mini | cheapest for Fido2 good amount of RKs (128) | no RK Management |
| Solo | Open Source hacker friendly | Not that many RKs (50) USB-C stability (according to others) interaction of LED with colored cases |
| Somu | Open Source hacker friendly Small size (for permanent attachment) | Not that many RKs (50) interaction of LED with colored cases |
| eWBM | Fido2 L2 A LOT of RKs (242) Fingerprint Sensor RK management | dependent on Bio Manager no updates (G450/G500) REALLY expensive RK management borked |
| Krypton | Free Solution Silent mode allows frictionless 2FA Open Source | Software-based means less potential Security Request notifs don't automatically go away Only works with browsers |
| Multipass | very versatile nowadays not as expensive | U2F only |
| Idem Card | very compact FIDO2 can use contact-chip as well as wireless methods Bluetooth | not cheap due to not supporting USB-HID compatibility limited (Windows 10 1903+ and mobile only) Intentionally against Spec Cannot be Updated |
| Ledger Nano S | DISPLAY (allows you to see where a request comes from) more uses than FIDO stuff UPDATES 6 colors | on retail price, definitely not cheap currently no FIDO2 clonable via Recovery seed |
Conclusion
To be updated
Simply said while I have to say that this article was more or less sparked by eWBM, I had something like this in mind for quite a while by now, and it's kinda weird to say that of all the possibilites, they certainly score top in Usability, even though not without their own problems. Generally I think that one cannot just declare one as a winner and the rest as losers or whatever, although when just looking at U2F/Fido2 the Yubikey series (both 4 and 5) are worst in price to performance, while the "Security Key" Lineup (just be careful you either get the one with a 2 marked into the plastic or the NFC version if you want Fido2) being a lot better with the "Security Key NFC" being a clear winner in price to performance (26,17€ plus shipping on mtrix) with the cheapest Fido2 device being the Solo for 20€ on amazon.de, the cheapest U2F device currently being the Hyperfido Mini with just 5,50€, although when just starting along or adding a bit of security without having to buy into anything, Krypton can be a nice solution.
Generally I think people should just choose what they want and I just try to provide details so users have a baseline what what can be chosen. Granted, there are a LOT more Devices available (for example the Hyperfido Mini Pro being the cheapest currently available FIDO2 device on amazon), which I don't have although I doubt there's too much difference between U2F Models, except for some rather small things.
Update Notes
22. January 2021
- Many New Keys (T1, Keepkey, Archos Safe-T Mini, BB02 Multi, Onlykey
- changed eWBM to eWBM/TrustKey G-Series
- minor adjustments
23. May 2020
- Added Feitian Multipass, GoTrust Idem Card and Ledger Nano S
- minor corrections
16. January 2020
- Added Somu, Blue Yubi and HyperFIDO Pro Mini
- eWBM RK Management is borked
15. January 2020
- Change eWBM stuff in regards to RK management
- a few other small things
5. January 2020
- Added HyperFIDO Mini and Krypton












How do Key-ID and Hypersecu HyperFIDO Mini relate? Are they made by the same company? They look very similar physically, but it sounds like there are two companies involved.
Thanks for your comment. really hard to get good ones here.
That's a really good question, I also kinda wondered this myself especially since Hypersecu also has an old model which looks the same as the old model key-ID.
on the internet i iirc read half an eternity that either or both are running Feitian firmware, and based on that I just looked a little further. Hypersecu calls their old model K5, which certainly looks similar to the model names of the FIDO Keys I have from Feitian, so a google search later, I found out that there actually is a Feitian K5. considering Feitian also has the K8 which looks basically the same as the HyperFIDO Minis (and by extension the Key-ID new model) I would hazard a guess that they licensed from Feitian.
on the other hand, Feitian lists Hypersecu but not Key-ID as partner so I cant say there isnt a relationship, although I would find it hard to believe that you can just sublicense that stuff.